(noun) securology.
Latin: se cura logia
Literally translated: the study of being without care or worry
Thursday, September 20, 2012
Tuesday, September 11, 2012
Lock Kill
Do you have a house/door key lock that you no longer want somebody to have the ability to unlock, but you don't have time to change the locks? Maybe you're a landlord? Or maybe you have some hidden purpose, such as forcing door traffic to a different entry to the building?
LockKill has a solution: a specialty key designed to slip in, bypass tumblers long enough to get all the way set, and then sheer off in place, destroying the lock. It only takes a few seconds.
Warning: the only real way of bringing that lock back from the dead is to replace it.
Watch the review by ITS Tactical:
LockKill has a solution: a specialty key designed to slip in, bypass tumblers long enough to get all the way set, and then sheer off in place, destroying the lock. It only takes a few seconds.
Warning: the only real way of bringing that lock back from the dead is to replace it.
Watch the review by ITS Tactical:
Saturday, September 8, 2012
Cognitive Side Channels
A recent media buzz this week involves so-called "side channel" attacks or leakages of information from human brain to computer interfaces. Not a ubiquitous technology today, but quite possibly down the road.
Essentially the attacks follow the lines of showing a plugged-in subject a bank, in which case the subject's mind races down the neural paths for things like account numbers, PINs, maybe balances or recent expenditures, etc. And the mere thoughts picked up by the device can capture these otherwise private thoughts inside the subject's brain.
Sound scary? It is. The brain wasn't designed to keep information from itself. Count us out of the "early adopter program".
Reminds us of the time the Ghostbusters were told the worst thing they could think of would be their next enemy:
Essentially the attacks follow the lines of showing a plugged-in subject a bank, in which case the subject's mind races down the neural paths for things like account numbers, PINs, maybe balances or recent expenditures, etc. And the mere thoughts picked up by the device can capture these otherwise private thoughts inside the subject's brain.
Sound scary? It is. The brain wasn't designed to keep information from itself. Count us out of the "early adopter program".
Reminds us of the time the Ghostbusters were told the worst thing they could think of would be their next enemy:
Friday, August 24, 2012
Protecting Cars from Viruses
Reuters is running a story that should amuse any computer security professional: Experts hope to shield cars from computer viruses.
An excerpt:
When you look at the statistics, you are far more likely to get injured or die in a car accident than you are in nearly any other security risk you face in your daily life. Even with the vast skies being what they are, and the regulations on the airlines industry and their pilots, it's not possible to keep air travel 100% safe, though it's safer than driving (once you get past the TSA checkpoint).
Computerized, self-driving cars may improve (emphasis on "may") safety stats; however, not if their software landscape looks like anything else we operate with a CPU in it these days. There are agencies with an operating budget larger than the GDP of several nations that are terrified about the possibility of malware injected into things like military aircraft or missile guidance systems. Given that, how in the world is an automobile for ~$20K (which is at most 1% of the price tag of the military's concerns) ever going to be 100% free of malware? Simple: it won't be.
We can't keep malware out of critical infrastructure SCADA systems. There's no way we can keep it out of your mom's minivan.
An excerpt:
Intel's McAfee unit, which is best known for software that fights PC viruses, is one of a handful of firms that are looking to protect the dozens of tiny computers and electronic communications systems that are built into every modern car.
Our guess is that when cars get to the point that they drive themselves, those who understand how malware works-- and more important: how undeniably complicated modern software and its hardware architecture can be-- will start donning a pair of Converse Chuck Taylors and resemble a modern Luddite by driving themselves, a la Will Smith in I, Robot.
It's scary business. Security experts say that automakers have so far failed to adequately protect these systems, leaving them vulnerable to hacks by attackers looking to steal cars, eavesdrop on conversations, or even harm passengers by causing vehicles to crash.
When you look at the statistics, you are far more likely to get injured or die in a car accident than you are in nearly any other security risk you face in your daily life. Even with the vast skies being what they are, and the regulations on the airlines industry and their pilots, it's not possible to keep air travel 100% safe, though it's safer than driving (once you get past the TSA checkpoint).
Computerized, self-driving cars may improve (emphasis on "may") safety stats; however, not if their software landscape looks like anything else we operate with a CPU in it these days. There are agencies with an operating budget larger than the GDP of several nations that are terrified about the possibility of malware injected into things like military aircraft or missile guidance systems. Given that, how in the world is an automobile for ~$20K (which is at most 1% of the price tag of the military's concerns) ever going to be 100% free of malware? Simple: it won't be.
Toyota Motor Corp, the world's biggest automaker, said it was not aware of any hacking incidents on its cars.
"They're basically designed to change coding constantly. I won't say it's impossible to hack, but it's pretty close," said Toyota spokesman John Hanson. [emphasis ours]Oh, we've never heard that before...
Officials with Hyundai Motor Co, Nissan Motor Co and Volkswagen AG said they could not immediately comment on the issue.
Mums the word is a much smarter response to the press.
A spokesman for Honda Motor Co said that the Japanese automaker was studying the security of on-vehicle computer systems, but declined to discuss those efforts.
A spokesman for the U.S. Department of Homeland Security declined to comment when asked how seriously the agency considers the risk that hackers could launch attacks on vehicles or say whether DHS had learned of any such incidents.They probably declined to comment because they are working on exploits for these as well. Say it ain't so? Look no further than Stuxnet and Flame, of which the US Gov takes full authorship credits. It's the future of the "cyberwarfarestate".
We can't keep malware out of critical infrastructure SCADA systems. There's no way we can keep it out of your mom's minivan.
Thursday, August 16, 2012
Classic Trust
 |
| Ken Thompson is on the left. That's not Adam Savage on the right. |
The moral is obvious. You can't trust code that you did not totally create yourself. (Especially code from companies that employ people like me.) No amount of source-level verification or scrutiny will protect you from using untrusted code. In demonstrating the possibility of this kind of attack, I picked on the C compiler. I could have picked on any program-handling program such as an assembler, a loader, or even hardware microcode. As the level of program gets lower, these bugs will be harder and harder to detect. A well installed microcode bug will be almost impossible to detect.Ken was referring to the trojan modifications he embedded into the C compiler, illustrating that you need to rely on more that source code, but the compiler, the assember, the loader, all the way down to the instruction sets of the CPUs. Or as Schneier famously pitched: "security is a chain; only as strong as its weakest link".
Who operates on a completely self-built system from software to hardware? We would venture to say: nary a soul.
Just a good reminder for a random Thursday, in case you forgot.
Labels:
complexity vs security,
history,
software security,
Trust
Monday, August 13, 2012
Hacking Hotels
 |
| Breaking into a hotel room with less than $50 in hardware |
The original author's documentation including the paper and slides are here.
Here's the simplified version:
- The vendor of the locks has an overwhelming majority of the market in the U.S. (chances are you stayed in a room that had this exact lock on it)
- The key cards use crypto for implementing the access control
- The mathematical aspect of the crypto is more or less fine (as is usually the case)
- The problem comes in managing keys (which is pretty much always the problem!)
- An administrative feature is easily exploited-- which is only slightly better than vendors shipping products with widely-known default passwords.
- An administrative maintenance device, when connected, can extract the crypto key and break the access control
- You can roll-you-own maintenance device on the very, very cheap
- Yes, this probably looks like a scene in any random Hollywood movie
- This will likely be a majorly expensive pain to fix for the vendor and hotels
- "Compensating controls" in this case include surveillance cameras, internal dead bolt manual locks, et al
Labels:
crypto,
key management,
penetration testing,
physical security
Wednesday, August 8, 2012
MS-CHAPv2 Crack
 It should come as no real surprise: MS-CHAPv2 is broken. It's an ancient scheme. If you were paying attention, you would have migrated your VPNs and Wireless networks away from it years ago anyway.
It should come as no real surprise: MS-CHAPv2 is broken. It's an ancient scheme. If you were paying attention, you would have migrated your VPNs and Wireless networks away from it years ago anyway.Here's a great break down of what this means to your wireless networks.
An even simpler one is to just note that these combinations are still fine:
- IPSEC and OpenVPNs are fine.
- WPA2 Enterprise wireless with PEAP is fine.
- WPA2 Non-Enterprise (i.e. home) wireless is fine (from this).
Labels:
complexity vs security,
crypto,
key management,
Marketing FUD
Tuesday, May 1, 2012
Skype Leak
Skype has had its moments in security history over the past several years, like the allegations that governments of certain countries have backdoors (not substantiating or denying those here), but now it appears that if you know a Skype username, you can find out the IP address of the user. Wow.
Saturday, April 21, 2012
Chances of Dying (InfoGraphic)
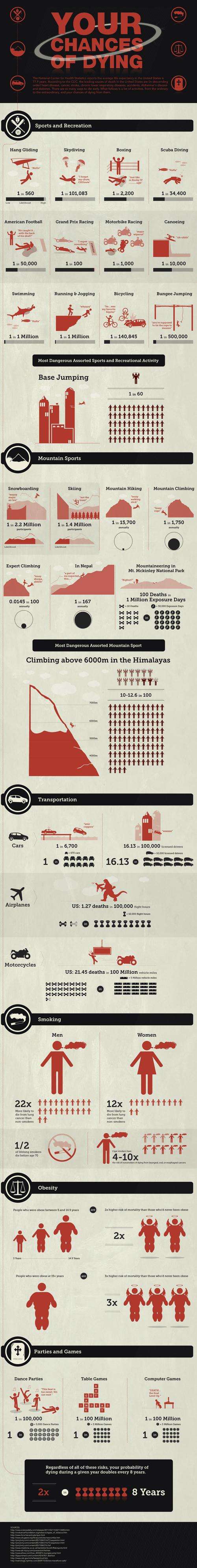
This is an interesting infographic that is floating around that depicts the statistical likelihood of dying from any given event.
It's a commonly known fact that societies tend to focus irrationally on certain threats over realistic ones, and this infographic just might help dispel some irrational fears that you hold.
For example, I was surprised to see that skydiving is less risky behavior than driving a car in traffic, which I do quite regularly. Looks like it may even be roughly as dangerous as flying commercially (well, except you probably won't have to deal with the TSA when you get on that prop plane at a small rural airport prepping for your skydive).
Note how dangerous any mountaineering is in Nepal. Ouch. Not great odds.
Tuesday, April 17, 2012
White Lies Affect Your Behavior
This is an interesting article about recent studies in the psychology of honesty and lies. Turns out that it's possible for a clever person to determine lies based on predictive human behavior under certain social obligations. In other words, the presence of the lie is leaked information, divulged by other events-- a great read for those curious of information flow theory as it implies to security.
Monday, April 16, 2012
Free OWASP .NET Development E-Book
For your developer friends (or you), Troy Hunt made his book about the OWASP Top 10 web security flaws as implemented in .NET available as a free e-book PDF. Plenty of good information in there to share with developers who need more clarification or a refresher in what it takes to build defensible web applications.
Friday, April 13, 2012
How To Send Digital Messages using HAM Radio
 This is a bit of a stretch from the normal topics, but in a severe disaster scenario (think Hurricane Katrina or third world country), it may be desired to send real time digital text communication when there is no communication infrastructure in place any longer (i.e. telephone lines are down and the Internet "tubes" were all clogged up).
This is a bit of a stretch from the normal topics, but in a severe disaster scenario (think Hurricane Katrina or third world country), it may be desired to send real time digital text communication when there is no communication infrastructure in place any longer (i.e. telephone lines are down and the Internet "tubes" were all clogged up).Here is a clever, low budget way to accomplish digital text communication over significant distances with very inexpensive components, namely a HAM radio, a netbook, an open source software application called FLDIGI, and a low tech way of connecting them together.
A clever improvement to this might be to encrypt the text data before its transmitted, which should be possible using a variety of tools, possibly even GnuPG (if the transmission medium is reliable enough to send the complete block of encrypted text without drops).
Wednesday, April 11, 2012
Measuring Wallets' Contents with Metal Detectors
 Turns out it may be more than RFID protection you may need for your wallet. New Scientist reports how some academics at University of Washington - Seattle can exploit some of the metallic features of dollar bills to count the money in your wallet. An excerpt:
Turns out it may be more than RFID protection you may need for your wallet. New Scientist reports how some academics at University of Washington - Seattle can exploit some of the metallic features of dollar bills to count the money in your wallet. An excerpt:They found an ordinary handheld metal detector was able to pick up a dollar bill from 3 centimetres away, and placing the notes behind plastic, cardboard and cloth did little to block the signal. Adding further bills in $5 increments increased the strength of the signal, making it is possible to count the number of bills, though converting this into an actual dollar value would be difficult as notes of different denominations contain the same amount of magnetic ink.Using larger metal detectors such as those found in airports should also increase the range of sensing, though detecting banknotes in such situations would be trickier as many other sources could interfere with the signal.
Saturday, April 7, 2012
Visa's New Data Center
 We just covered the NSA's new data center, so it seems appropriate to mention Visa's new data center, complete with a moat!
We just covered the NSA's new data center, so it seems appropriate to mention Visa's new data center, complete with a moat! Notice how castle features are still king for physically securing our data in the information age.
An excerpt:
The 8-acre facility looks like any other industrial park in a sleepy suburb. But the serene setting masks hundreds of cameras and a crack team of former military personnel. Hydraulic bollards beneath the road leading to the OCE can be quickly raised to stop an intruding car going 50 mph. Any speed faster, and the car can't navigate a hairpin turn, sending it into a drainage pond that functions as a modern-day moat.Here is the exact location of the data center. So much for trying to hide from Google Maps!
The data center resembles a fortress, with dogged attention to detail. It can withstand earthquakes and hurricane-force winds of up to 170 mph. A 1.5-million-gallon storage tank cools the system. Diesel generators onsite have enough power, in the event of an outage, to keep the center running for nine days. They generate enough electricity for 25,000 households.
Once you get clearance from a guard station, get an OK from a roving security guy in a golf cart, and surrender a photo and fingerprint inside, the adventure begins.
View Larger Map
Saturday, March 31, 2012
Stanford University Online Cryptography Course
 Stanford University has a free online Cryptography Course. Looks very interesting for someone who wants to peel back the layers of the onion, but isn't scared off by the math. (Many applied cryptographers aren't necessarily experts in the theoretical mathematical aspects and vice versa.)
Stanford University has a free online Cryptography Course. Looks very interesting for someone who wants to peel back the layers of the onion, but isn't scared off by the math. (Many applied cryptographers aren't necessarily experts in the theoretical mathematical aspects and vice versa.)Professor Dan Boneh gives an introduction to the course:
Thursday, March 29, 2012
Using VPNs to Bypass Content Restrictions

Some content providers, like Hulu, have restrictions on certain content to make it only available in specific countries. They implement these policy goals in the form of restricting access to foreign-looking IP addresses.
If you are behind a foreign IP address and wish to view the content anyway, the current solution is to just use a VPN service to appear local.
Labels:
content filtering,
Digital Rights Management,
humor,
privacy
Thursday, March 22, 2012
In Memory: Bill Zeller
 Having just caught up on the positive achievements of Alex Halderman, we have discovered that another promising young mind has been lost forever.
Having just caught up on the positive achievements of Alex Halderman, we have discovered that another promising young mind has been lost forever.Bill Zeller was also a member of Ed Felten's Freedom to Tinker crew and a PhD student at Princeton. Bill also is known for creating MyTunes, which was one of the first implementations to prove Digital Rights Management (DRM) is really the emperor without clothes.
You can read Bill's tragic story here, or his own words here. Even by those who did not directly know him, he will be missed.
Wednesday, March 21, 2012
Alex Halderman on Internet Voting
 Computer Science Professor J. Alex Halderman is an upcoming academic star that we at Securology have been watching for awhile now, since some of the earliest days of all the great work put on at Princeton by Ed Felten and his Freedom to Tinker group (an excellent blog). Halderman, having completed his PhD (Bell Labs UNIX and C programming language creator Brian Kernighan was on his PhD committee!), has moved on to the University of Michigan as a member of the faculty and is continuing his excellent work at the intersection of technology and public policy, which always means security and privacy issues are in the spotlight.
Computer Science Professor J. Alex Halderman is an upcoming academic star that we at Securology have been watching for awhile now, since some of the earliest days of all the great work put on at Princeton by Ed Felten and his Freedom to Tinker group (an excellent blog). Halderman, having completed his PhD (Bell Labs UNIX and C programming language creator Brian Kernighan was on his PhD committee!), has moved on to the University of Michigan as a member of the faculty and is continuing his excellent work at the intersection of technology and public policy, which always means security and privacy issues are in the spotlight.
Here is an excellent interview with Halderman (presumably shot at the 2012 RSA Conference) on how he and his students (legally) hacked the mock trial of Internet Voting put on by Washington D.C., and why Internet Voting should not be employed for a very long time.
In summary, there are two main reasons why Internet Voting is a horrible idea:
- Getting the software perfectly correct is, for all intents and purposes, impossible.
- Authenticating a voter eliminates the ability to anonymize the voter's vote (major privacy flaw).
Labels:
anonymity,
malware,
research,
software security
Sunday, March 4, 2012
Detecting Social Network Connectivity
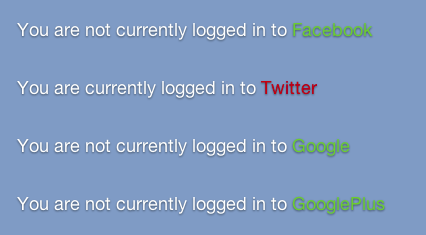 This is a creative implementation that discovers several information flow theory violations. The end result is a website that is not part of a given social network can tell if a connected user is logged into the social network.
This is a creative implementation that discovers several information flow theory violations. The end result is a website that is not part of a given social network can tell if a connected user is logged into the social network.Check out the demo to see what your browser reveals.
Labels:
complexity vs security,
privacy,
software security,
Trust
Thursday, March 1, 2012
Brute Forcing Credit Card Numbers
 PCI Regulations allow merchants to store the first 6 digits plus the last 4 digits of a customer's credit card number. Ever wonder just how secure that is?
PCI Regulations allow merchants to store the first 6 digits plus the last 4 digits of a customer's credit card number. Ever wonder just how secure that is?Well, without knowing anything else, if a credit card is stored as 1234-56xx-xxxx-1234, the possible missing middle digits range from 00-0000 to 99-9999, roughly one million (1,000,000) possible combinations. That seems very tough to guess (without being detected).
However, credit card numbers all implement Luhn's Algorithm, which is a special mathematical formula that uses the last digit in the number as a check digit. Not all of the 1,000,000 middle combinations will pass Luhn's check. Turns out (since modulus 10 math is involved), the quantity of missing middle number combinations is at most 100,000 possibilities, not a million. Luhn's reduces the complexity by an order of magnitude.
So, what if an attacker can get just one more digit somehow? Well, it's only 10^4 combinations then: 10,000 possibilities. What if they can get two more digits? The math follows this formula: 10 ^ (n-1). Here's the table:
6 digits
|
10 ^5 = 100,000
|
5 digits
|
10^4 = 10,000
|
4 digits
|
10^3 = 1,000
|
3 digits
|
10^2 = 100
|
2 digits
|
10^1 = 10
|
1 digit*
|
10^0 = 1
|
* It makes sense, if you're missing a single digit, Luhn's will help you recover it. That is the purpose of that algorithm originally.
Now, as far as practical applications for abusing the knowledge of Luhn's Algorithm on a PCI acceptably-formatted credit card number are concerned ... 100,000 attempted transactions to brute force a card number by a single merchant will certainly be detected and the merchant's ability to process any transaction will be in jeopardy. So, an attacker with access to a merchant account is probably not a valid threat to model.
For an attacker to attempt to make purchases at varying merchants with this brute force scheme and everything but the middle 6 digits, the attacker will also have to have the billing address and potentially the CVV code. That makes the problem significantly harder. But as the attacker can discover missing digits from the middle six, the problem becomes easier. If the victim is well chosen, and the attacker can do something like shoulder surf at a point of sale machine to visually see and remember a digit or two or three, then the problem gets noticeably easier. If the attacker can do that, the attacker can probably also guess the billing address and name. There's still that pesky CVV code, though (that's another 3 digits which compounds things).
Realistically, though, for an attacker to get that much information on a victim, the victim would probably have to be oblivious or have an extremely large line of credit to make it worthwhile.
For the rest of us, we're fairly safe with the PCI rules of first 6 plus last 4 digits being public knowledge.
Check this out for yourself. Here's the source code for a very simple C# console application that will take whatever first 6 plus last 4 digits you provide it, and churn out all of the possible middle combinations. Here is the inspiration for the C# Luhn's implementation. [Sorry about the code formatting.]
using System;
using System.Linq;
namespace Luhn
{
public class Luhn
{
private static int _middle = -1;
private static int _counter;
private static int _places;
public static void Main(string[] args)
{
if (!args.Any())
{
PrintUsage();
return;
}
var cc = args[0].Replace("-", "").Replace(" ", "").Replace("x", "X");
if (cc.Length != 16)
{
Console.WriteLine("input is not correct length.");
PrintUsage();
return;
}
_places = cc.Length - cc.Replace("X", "").Length;
var limit = Math.Pow(10, _places);
Console.WriteLine("Places: {0}", _places);
Console.WriteLine("Limit: {0}", limit);
while (_middle < limit)
{
var s = FindNext(cc);
if (!PassesLuhnCheck(s)) continue;
Console.WriteLine("Valid: {0}", s);
_counter++;
}
Console.WriteLine("\r\nFound {0} potential matches for {1}", _counter, args[0]);
}
private static void PrintUsage()
{
Console.Write("Usage: luhn.exe [credit card number]\r\n"
+ " in format like 1234-56xx-xxxx-1234\r\n"
+ " or like 1234-5678-xxxx-1234, etc.\r\n\r\n");
}
private static string FindNext(string number)
{
_middle++;
var middle = _middle.ToString();
while (middle.Length < _places)
{
middle = "0" + middle;
}
return (number.Replace(GetPlaceHolder(), middle));
}
private static string GetPlaceHolder()
{
var s = "";
for (var i = 0; i < _places; i++)
{
s += "X";
}
return s;
}
private static bool PassesLuhnCheck(string number)
{
var deltas = new[] { 0, 1, 2, 3, 4, -4, -3, -2, -1, 0 };
var checksum = 0;
var chars = number.ToCharArray();
for (var i = chars.Length - 1; i > -1; i--)
{
var j = chars[i] - 48;
checksum += j;
if (((i - chars.Length) % 2) == 0)
checksum += deltas[j];
}
return ((checksum % 10) == 0);
}
}
}
Subscribe to:
Posts (Atom)






